In the world of Linux, understanding file systems and permissions is fundamental to effectively managing data and ensuring security within the system. This segment introduces various commands, concepts, and best practices associated with file systems, permissions, and ACLs.
The file system in Linux follows a hierarchical structure, starting from the root directory (/) and branching into various directories like /bin, /usr, /home, /etc, and more. These directories hold crucial binaries, user data, configuration files, and system-related information, defining the organization of data within a Linux system.
File permissions in Linux are classified into three levels: owner, group, and others, represented by read (r), write (w), and execute (x). Understanding these permissions is crucial as they govern access to files and directories, ensuring data integrity and security.
Commands like chmod, chown, and chgrp facilitate changing access permissions and ownership for files and directories. By using these commands, administrators can assign specific access levels to users and groups, enhancing data security and access control.
Access Control Lists (ACLs) extend the standard file permissions in Linux, offering more detailed and granular control over file access. ACLs enable administrators to define permissions for individual users or groups, expanding the flexibility and precision of access management.
File Systems Permissions and Ownership
File System Hierarchy:
Linux follows a hierarchical file system structure, starting from the root directory / and branching into various directories:
Root Directory (/): The top-level directory containing all other directories and files.
/bin, /sbin, /usr, /etc: Directories holding essential binaries, system binaries, user binaries, and system configuration files, respectively.
/home: Houses user home directories.
/var: Contains variable files like logs, databases, mail, and more.
/tmp: Used for temporary files.
/opt: Optional software applications often reside here.
/dev: Device files for hardware components.
/proc: Virtual file system that provides access to kernel and process information.
File Permissions and Ownership:
Linux file permissions are categorized into three levels: owner, group, and others. These permissions are represented by read (r), write (w), and execute (x).
Types of Permissions:
Read (
r): Allows reading and viewing the contents of a file or directory.Write (
w): Permits modifying, appending, or deleting a file's contents, and creating or deleting files within a directory.Execute (
x): Grants the ability to execute files or traverse through directories.
Let's use an example to illustrate this:
To change the access permissions of files
Chmod is the command used to change the access permissions of a file.
chmod
Example:
rwx rwx rwx
In that values are r=4,w=2,x=1 so 4+2+1=7 then total value is 777
chmod 777 permission says all permission are given like we read, write and execute
chmod 777 test-file.txt
The command chmod 777 test-file sets the access permissions of the file test-file to read, write, and execute for the owner, group, and others.

chmod 600 filename
To give read and write permissions to the owner, and no permissions to group and others
chmod 750 filename
To give full permissions (read, write, and execute) to the owner, and read and execute permissions to the group, and no permissions to others
chmod 700 filename
To give full permissions (read, write, and execute) to the owner, and no permissions to the group and others:
chmod 444 filename
To give only read permissions to the owner, group, and others. not write and execute permissions to owner, group and others.
or you can simply says: to remove write and execute permissions from the owner, group, and others
This permission setting is commonly used when you want to make a file read-only for everyone, preventing any modifications or execution.
Now, let start deeply discuss file access permission.
chmod 755 filename
To give read, write, and execute permissions to the owner, and read, execute permission to group and others
Let's break down the permission code:
The leftmost digit,
7, represents the permission for the owner of the file.The middle digit,
5, represents the permission for the group that the file belongs to.The rightmost digit,
5, represents the permission for other users (not the owner or group).
Each digit in the permission code represents a combination of read (4), write (2), and execute (1) permissions.
Here's a breakdown of the permission codes:
7: This grants the owner of the file full permissions, which include read, write, and execute.5: This grants the group read and execute permissions, but not write permissions.5: This grants other users read and execute permissions, but not write permissions.
In summary, executing chmod 755 filename sets the file permissions as follows:
The owner of the file has full control (read, write, and execute).
The group has read and execute permissions.
Other users have read and execute permissions.
This permission setting is commonly used for executable files or scripts that should be readable and executable by all users, but not writable to maintain security.
Chown Command file Permissions:
chown Command:
chown stands for "change owner" and is used to change the owner of a file or directory.
sudo chown new_owner filename
new_owner: The new user or user ID to assign as the owner.file(s): The file or list of files/directories to which ownership will be changed.
Example:
Let's assume you want to change the owner of a file named test-file.txt to a user named niloy [ my younger brother name ]:
sudo chown niloy test-file.txt

Here, after executing the "ls -l" command, we noticed that the owner of our test-file.txt is 'ubuntu,' right?
Now, let's change the file owner from the 'ubuntu' user to a new user named 'niloy' and grant permission.
Let's attempt to implement this.
sudo chown niloy test-file.txt
After executing this command, we see an error message stating "invalid user" because we don't have any user named 'niloy.' So, first, let's create a user named 'niloy,' and then let's try again to see if we can change the file's owner.

After creating the user, when we execute the same command, we can observe that the file's owner name has indeed been changed.

chgrp group Ownership file Permissions :
chgrp Command:
chgrp stands for "change group" and is used to change the group ownership of a file or directory.
chgrp new_group filename
new_group: The new group or group ID to assign as the group owner.file(s): The file or list of files/directories to which group ownership will be changed.
Example:
Changing the group ownership of the test-file.txt file to newgroup:
chgrp newgroup test-file.txt

Here, after executing the "ls -l" command, we noticed that the group of our test-file.txt is 'ubuntu,' right?
Now, let's change the file group from the 'ubuntu' user to a new user named 'niloy' and grant permission.
Let's attempt to implement this.
We had created a new user named 'niloy' earlier to change the file's owner, right?
We know that when creating any user, a default group with the same name is automatically created for that user.
To verify this, we executed the following command.
id niloy

After executing it, we observed that 'niloy' indeed has a default group.
So now, we will change the group ownership of our file to a new group named 'niloy' using the command below.
sudo chgrp niloy test-file.txt
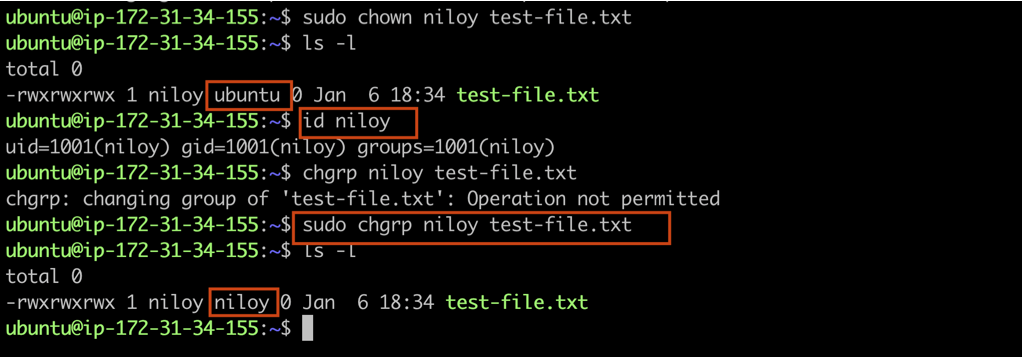
Now, after running the 'ls -l' command again, we can see that the group owner of our file 'test-file.txt' has changed.
Permissions and Use Cases:
File Ownership Change: Use
chownwhen you want to change both the user and group ownership of a file or directory.Group Ownership Change: Use
chgrpwhen you only want to modify the group ownership without altering the user owner.
These commands are typically used by system administrators to manage file and directory ownership, especially when users need access to specific files or when group permissions require modification for collaboration purposes. Proper ownership and group assignments are critical for effective access control and data security in Linux systems.
Access Control Lists (ACLs)
Access Control Lists (ACLs) in Linux are an extension of the standard file permission system, allowing for more granular control over access to files and directories. ACLs enable you to define permissions for specific users or groups beyond the traditional owner, group, and others classifications. They provide a finer level of access control and are useful in multi-user environments or when more complex permission settings are required.
Usage of ACLs:
Viewing ACLs:
To view ACLs for a file or directory, use the getfacl command:
$getfacl filename
We've previously applied file permissions to the file named 'test-file'.
Now, we'll use the 'getfacl' command to check the permissions of this file. This command will display the file name, the file's user owner, group owner, and the permissions represented by 'read' (r), 'write' (w), and 'execute' (x) for three categories: owner, group, and others.
For example---
getfacl test-file.txt
file: test-file.txt
owner: niloy
group: niloy
user::rwx
group::rwx
other::rwx

After executing the command "getfacl test-file.txt," we noticed in the terminal that the command "getfacl" wasn't found but suggested to be installed with: "sudo apt install acl."
Since we need the 'acl' command to check permissions, we must install 'acl' first. Therefore, let's execute the following command:
sudo apt install acl
Now, we'll execute the command "getfacl test-file.txt" again to check the information related to the "test-file.txt" file.

Once executed, it will display all the information about the file, including its name, owner's name, group's name, and permission categories for users, groups, and others.
For a clearer understanding of ACL permissions, let's create a new file named "nahid-test-file.txt."

Now, to view the access control list of this file, we'll execute the command 'getfacl nahid-test-file.txt.'
getfacl nahid-test-file.txt

After execution, we see that the owner and group name of this file are 'ubuntu' because, by default, we're working in the 'ubuntu' environment. Also, observing the permissions of this file, we find that both the owner and group have read and write permissions, while others have only read permissions.
Setting ACLs:
setfacl command
The setfacl command is used to set or modify ACLs for files and directories:
If we want to modify our file's permissions easily, we'll use the "setfacl" command:
setfacl -m u:username:permissions filename
Let's add a new user for our file and grant full permissions to that user using the "setfacl" command.
For instance, we'll assign a new user named "nahid" for our file and grant full permissions to that user.
sudo setfacl -m u:nahid:rwx nahid-test-file.txt

The issue here is that we haven't created a user named "nahid" yet, so I've faced this problem. Thus, I'll create the "nahid" user now.
After executing the command, we can see that the new user named "nahid" has been given "rwx" full permissions.

Removing ACL Entry:
Remove an ACL entry for a user on a file:
setfacl -x u:username filename
Now, if we want to remove the "nahid" user specifically for this file, we'll use the following command:
sudo setfacl -x u:nahid nahid-test-file.txt

After executing the removal command, we can observe that the user list for this specific file no longer shows any user named "nahid," meaning that there are no permissions for the "nahid" user for this file.
ACLs provide a powerful means of managing access control in Linux, allowing administrators to define fine-grained permissions for users and groups. They are particularly useful in scenarios where more detailed access control is required beyond the scope of standard permissions. However, they should be used thoughtfully and documented carefully to maintain system security and integrity.
Understanding file systems and permissions in Linux is indispensable for managing a system's data, ensuring privacy, and maintaining security. The introduced commands - chmod, chown, chgrp, and ACL-related commands - provide the means to control access, assign ownership, and manage file permissions in a detailed manner.
File systems, with their hierarchical organization, provide a structured approach to data storage, allowing for systematic management of essential system files, user data, configurations, and more.
Through proper utilization of file permissions, administrators can control who can access, modify, or execute specific files and directories, thereby safeguarding sensitive data and maintaining system integrity.
Access Control Lists (ACLs) elevate access management by providing finer control, enabling administrators to define permissions for individual users or groups beyond the standard file permissions. They offer an enhanced level of security and access customization in multi-user environments or complex access control scenarios.
In conclusion, mastering file systems, permissions, and ACLs is vital for effective Linux system administration, ensuring efficient data management, access control, and system security.
Thank you for reading this blog. I hope you learned something new today! If you found this blog helpful, please like, share, and follow me for more blog posts like this in the future.
— Happy Learning !!!
Let’s connect!!!!
